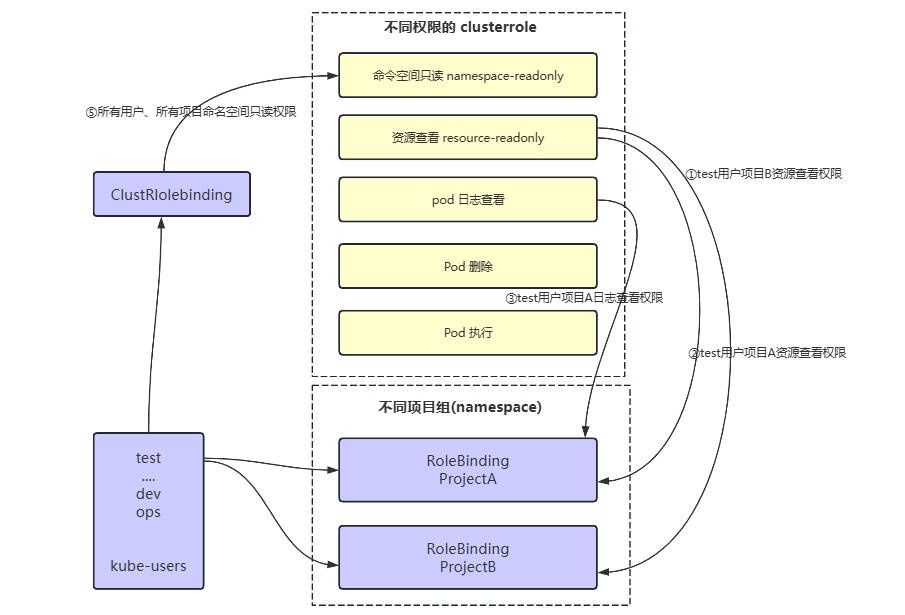
# K8s 细粒度权限控制 RBAC
![rbac.jpg]()
# 1. 创建不同权限的 clusterrole
# 1.1 命令空间只读 namespace-readonly
| $ cat namespace-readonly.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRole |
| metadata: |
| name: namespace-readonly |
| rules: |
| - apiGroups: |
| - "" |
| resources: |
| - namespaces |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - metrics.k8s.io |
| resources: |
| - pods |
| verbs: |
| - get |
| - list |
| - watch |
# 1.2 资源查看 resource-readonly
| $ cat resource-readonly.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRole |
| metadata: |
| name: resource-readonly |
| rules: |
| - apiGroups: |
| - "" |
| resources: |
| - configmaps |
| - endpoints |
| - persistentvolumeclaims |
| - pods |
| - replicationcontrollers |
| - replicationcontrollers/scale |
| - serviceaccounts |
| - services |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - "" |
| resources: |
| - bindings |
| - events |
| - limitranges |
| - namespaces/status |
| - pods/log |
| - pods/status |
| - replicationcontrollers/status |
| - resourcequotas |
| - resourcequotas/status |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - "" |
| resources: |
| - namespaces |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - apps |
| resources: |
| - controllerrevisions |
| - daemonsets |
| - deployments |
| - deployments/scale |
| - replicasets |
| - replicasets/scale |
| - statefulsets |
| - statefulsets/scale |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - autoscaling |
| resources: |
| - horizontalpodautoscalers |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - batch |
| resources: |
| - cronjobs |
| - jobs |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - extensions |
| resources: |
| - daemonsets |
| - deployments |
| - deployments/scale |
| - ingresses |
| - networkpolicies |
| - replicasets |
| - replicasets/scale |
| - replicationcontrollers/scale |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - policy |
| resources: |
| - poddisruptionbudgets |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - networking.k8s.io |
| resources: |
| - networkpolicies |
| verbs: |
| - get |
| - list |
| - watch |
| - apiGroups: |
| - metrics.k8s.io |
| resources: |
| - pods |
| verbs: |
| - get |
| - list |
| - watch |
# 1.3 pod 日志查看
| $ cat pod-log.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRole |
| metadata: |
| name: pod-log |
| rules: |
| - apiGroups: |
| - "" |
| resources: |
| - pods |
| - pods/log |
| verbs: |
| - get |
| - list |
| - watch |
# 1.4 Pod 删除
| $ cat pod-delete.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRole |
| metadata: |
| name: pod-delete |
| rules: |
| - apiGroups: |
| - "" |
| resources: |
| - pods |
| verbs: |
| - get |
| - list |
| - delete |
# 1.5 Pod 执行
| $ cat pod-exec.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRole |
| metadata: |
| name: pod-exec |
| rules: |
| - apiGroups: |
| - "" |
| resources: |
| - pods |
| verbs: |
| - get |
| - list |
| - apiGroups: |
| - "" |
| resources: |
| - pods/exec |
| verbs: |
| - create |
# 1.6 创建不同权限的 clusterrole
# 2. 创建 serviceaccount
| $ kubectl create ns kube-users |
| |
| $ kubectl create sa test -n kube-users |
| $ kubectl create sa dev -n kube-users |
| $ kubectl create sa ops -n kube-users |
| |
| $ kubectl create token test -n kube-users |
| $ kubectl create token dev -n kube-users |
| $ kubectl create token ops -n kube-users |
# 3. 创建 ClusterRoleBinding
# 3.1 绑定全局命名空间查看权限
| $ cat clusterrolebinding-namespace-readonly.yaml |
| apiVersion: rbac.authorization.k8s.io/v1 |
| kind: ClusterRoleBinding |
| metadata: |
| name: clusterrolebinding-namespace-readonly |
| subjects: |
| - kind: Group |
| name: system:serviceaccounts:kube-users |
| apiGroup: rbac.authorization.k8s.io |
| roleRef: |
| kind: ClusterRole |
| name: namespace-readonly |
| apiGroup: rbac.authorization.k8s.io |
| |
| $ kubectl apply -f clusterrolebinding-namespace-readonly.yaml |
# 3.2 绑定日志查看权限
| $ kubectl create rolebinding ops-pod-log --clusterrole=pod-log --serviceaccount=kube-users:ops --namespace=projectA |
| $ kubectl create rolebinding ops-pod-log --clusterrole=pod-log --serviceaccount=kube-users:ops --namespace=projectB |
# 3.3 绑定资源查看权限
| $ kubectl create rolebinding ops-resource-readonly --clusterrole=resource-readonly --serviceaccount=kube-users:ops --namespace=projectA |
| $ kubectl create rolebinding ops-resource-readonly --clusterrole=resource-readonly --serviceaccount=kube-users:ops --namespace=projectB |
# 3.4 绑定 Pod 执行权限
| $ kubectl create rolebinding ops-pod-exec --clusterrole=pod-exec --serviceaccount=kube-users:ops --namespace=projectA |
| $ kubectl create rolebinding ops-pod-exec --clusterrole=pod-exec --serviceaccount=kube-users:ops --namespace=projectB |
# 3.5 绑定 Pod 删除权限
| $ kubectl create rolebinding ops-pod-delete --clusterrole=pod-delete --serviceaccount=kube-users:ops --namespace=projectA |
| $ kubectl create rolebinding ops-pod-delete --clusterrole=pod-delete --serviceaccount=kube-users:ops --namespace=projectB |
本文出自于:https://edu.51cto.com/course/23845.html